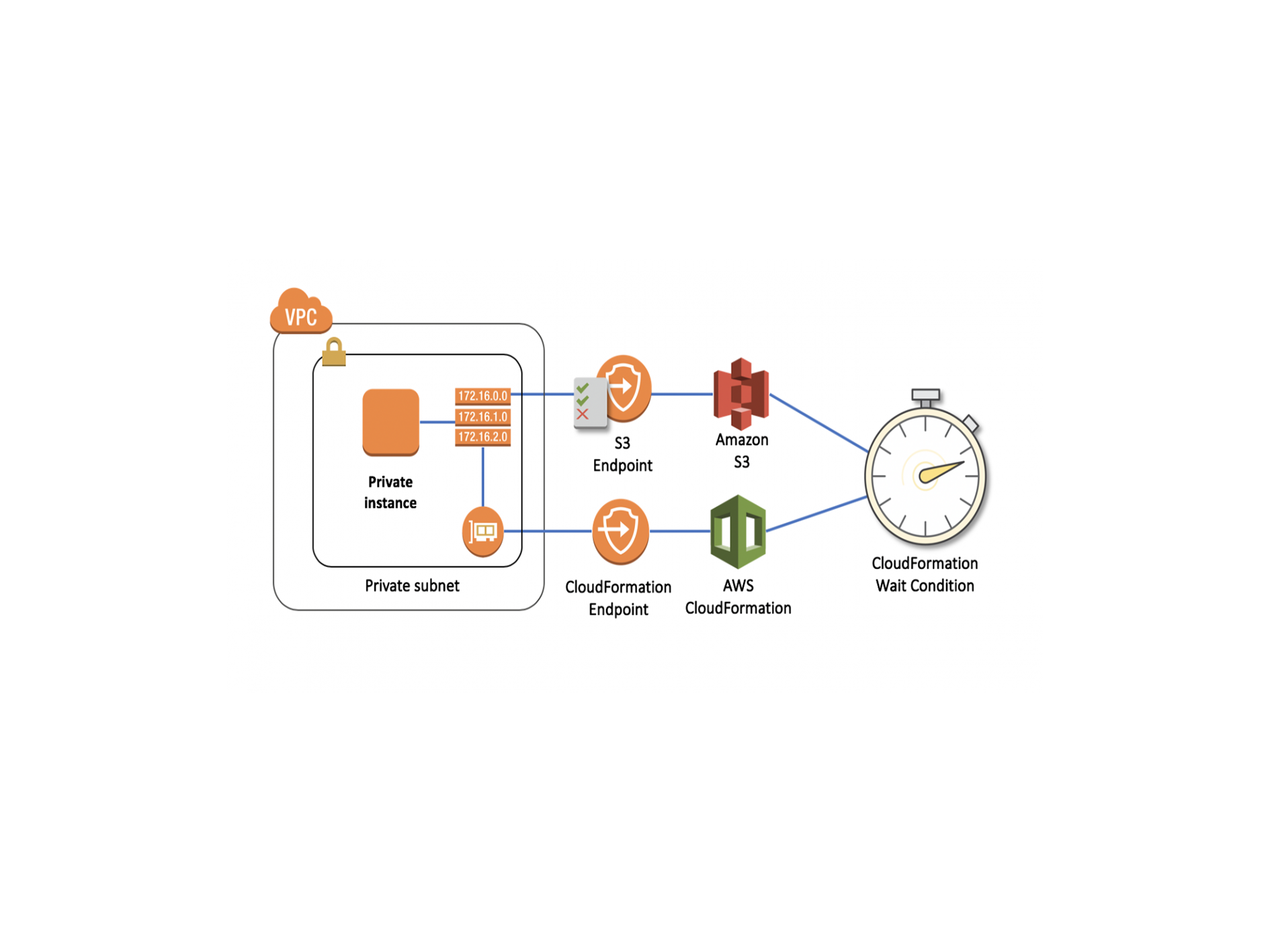
You can improve the security posture of your VPC by configuring AWS CloudFormation to use an interface VPC endpoint. Interface endpoints are powered by PrivateLink, a technology that enables you to privately access CloudFormation APIs by using private IP addresses. PrivateLink restricts all network traffic between your VPC and CloudFormation to the Amazon network. Also, you don’t need an Internet gateway, a NAT device, or a virtual private gateway.
NB: You aren’t required to configure PrivateLink, but it’s recommended.
NOTE THIS:
Before you configure the VPC endpoints for CloudFormation, consider the following.
When you are using the VPC endpoint feature, you need to grant access to CloudFormation-specific S3 buckets for the resources in a VPC that must respond to a custom resource request or a wait condition.
If you use CloudFormation to create resources in the VPC with a VPC endpoint, you will need to modify your IAM endpoint policy so that it permits access to certain S3 buckets.
CloudFormation has S3 buckets in each Region to monitor responses to a custom resource request or a wait condition, so if a template includes custom resources or wait conditions in a VPC,
the VPC endpoint policy must allow users to send responses to the following buckets:
- For custom resources, permit traffic to the
cloudformation-custom-resource-response-regionbucket. If you are using a custom resources, do not add dashes to the region names. instead, do this; eg.uswest2. - For wait conditions, permit traffic to the
cloudformation-waitcondition-regionbucket. When using wait conditions, region names do contain dashes. For example,us-west-2. If the endpoint policy blocks traffic to these buckets, CloudFormation cannot receive responses and the stack operation will fail. Example, if you have a resource in a VPC in theus-west-2Region that must respond to a wait condition, the resource must be able to send a response to thecloudformation-waitcondition-us-west-2bucket. - VPC endpoints currently don’t support cross-Region requests. But make sure that you create your endpoint in the same Region in which you plan to issue your API calls to CloudFormation.
- VPC endpoints only support Amazon-provided DNS through Route 53, therefore if you want to use your own DNS, you can use conditional DNS forwarding.
- The security group attached to the VPC endpoint must allow incoming connections on port 443 from the private subnet of the VPC.
Creating the VPC EndPoint for AWS CloudFormation
To create the VPC endpoint for the CloudFormation service, you can use the Creating an interface endpoint procedure in the Amazon VPC User Guide to create the following endpoint:
eg. com.amazonaws.region.cloudformation
region represents the region identifier for an AWS Region supported by CloudFormation, such as us-east-2 for the US East (Ohio) Region.
Thank you for taking the time to read this blog post. Kindly share and give us your feedback on how best we can improve our contents.